In a previous article, I showed you how to create an app registration in Azure AD. App registrations have a wide variety of use cases but one of the most powerful for MSPs is being able to run powershell across all customers under management. In this article, I am going to show you how to leverage the App registration you created to establish tokens for secure access to customers. With these tokens you will be able to run a single powershell script against all of your customers in Partner Center.
Prerequisites
- App Registration is completed in your Azure AD environment (check out my previous post here)
- Indirect reseller with Microsoft
- You have delegated admin rights across all customers you manage in Partner Center
- Proficient in PowerShell (You are not likely to have a good time long-term if you don’t understand the fundamentals of PowerShell)
Secure Application Model
Before I provide you the script you can run, I wanted to quickly touch on the Secure Application Model. SAM was created by Microsoft and it can be leveraged so that we can establish a secure, headless connection to customers under management. Headless means we can connect to our customers without having to type in a username and password. It leverages a token based architecture instead to grant access to resources.
Tokens generated here can be used to tap into certain modules like MSOnline, AzureAD, and ExchangeOnline across all customers. Below I will be showing you how to generate these tokens. Much of this content can be contributed to Kelvin Tegalaar, a Microsoft MVP who has created tons of scripts off this model.
Generating Tokens
The link above will take you to a Github page with the script you can run to generate tokens.
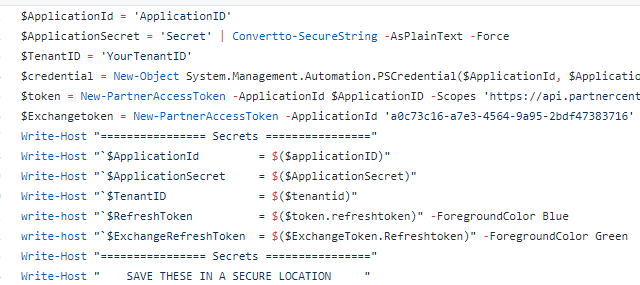
The Application ID and Secret will be from your App registration you copied in my last post. The tenantID will be your tenant ID that is linked to Partner Center
When you run this script, you will be asked to sign in with a Global Admin for the refresh token and then you will be given a URL and code to generate the ExchangeOnline token
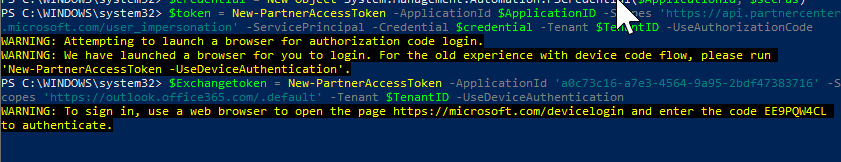
If you have entered in the correct code, you will get a success message and the PowerShell script will complete, providing you with the appropriate tokens.

Sample Script
To conclude here, I wanted to provide you a script that leverages this model and tokens you just created.
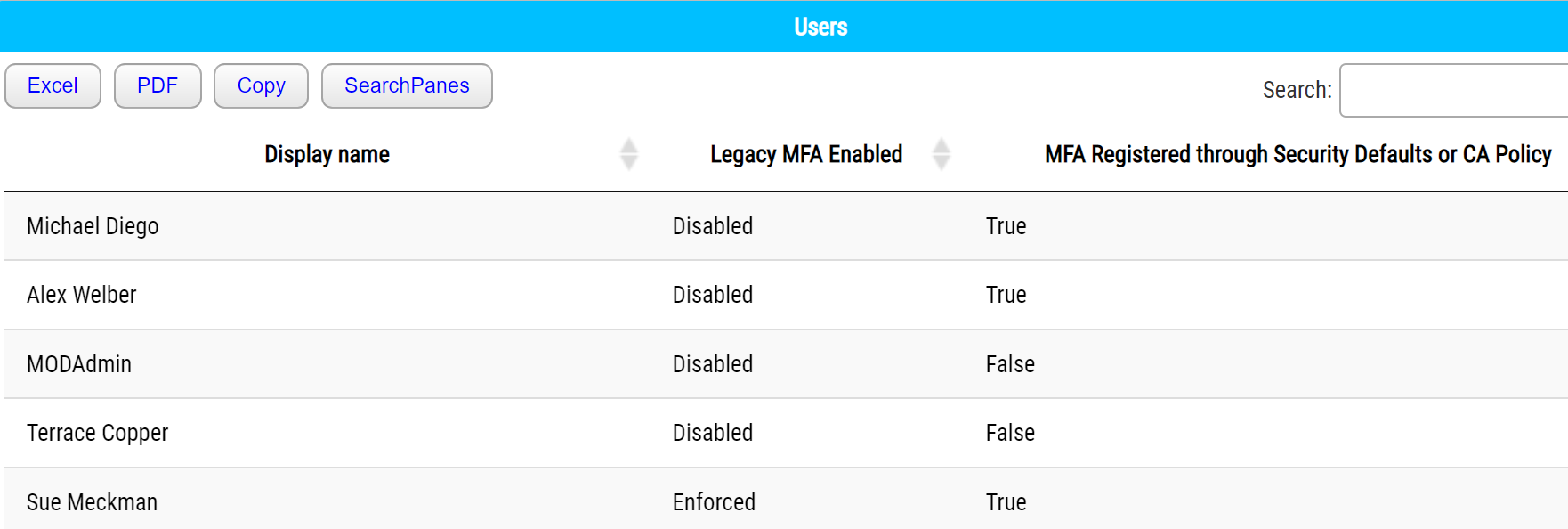
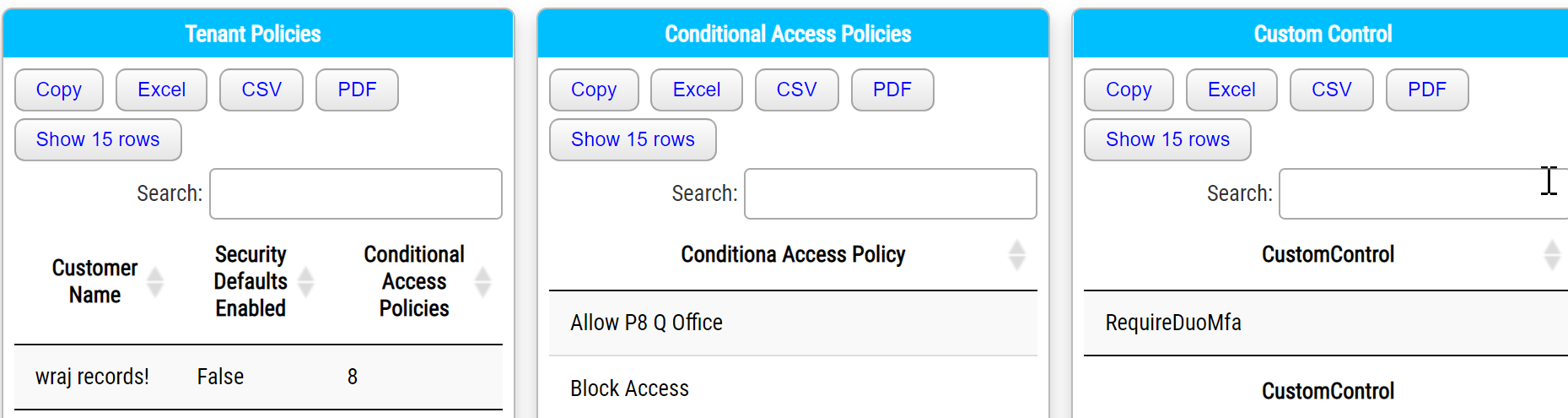
The script uses the Secure Application Model to connect to your client environments and creates HTML pages that list the following:
- MFA enforced through the MFA portal
- Conditional Access Policies
- Security Defaults (enabled or disabled)
- Custom Controls (ex. DUO)
Each customer will have their own page.
Final Thoughts
Leveraging the Secure Application model is a great way to create automation across the tenants you manage. It is great for pulling periodic reports like we did above as well as implementing new policies or configurations. In a future article, I will show you how to leverage Microsoft’s graph API as well to perform even more management than PowerShell can provide.
