In previous blog post, I have talked about best practices around Safe Links and Safe Attachments policies with Microsoft. Both of these policies are configurable if you have Defender for Office 365. Ultimately they provide pre-and post- email protection against malicious links or attachments that may get sent to a user. This type of protection can greatly help an organization reduce risk around phishing incidents.
As an MSP, you want to understand if you have set up these types of policies across your customer environments. For this reason, I created a script that leverages the Secure Application model to connect to Exchange across all of your customer environments and report on if these policies are in place.
Prerequisites
You will need to garner tokens and GUIDs from both the Secure Application Model. The secure application model allows for a headless connection into all of your customer environments. The script to run that can be found from Kelvin over at CyberDrain. Click here to go to that page in Github.
The Script
Clicking on the icon above will bring you to the script published in GitHub. You can download this script locally and update it with your personal secrets or follow the prompts to enter your secrets if you run it without any modifications:
When the script begins to run, it will loop through all of your customer environments to look and see if there is an active Safe Link and Safe Attachment policy. After it has checked for one customer, it will remove the Exchange session and move on to the next customer:
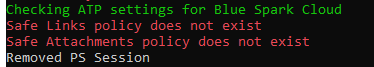
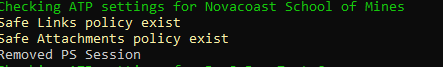
When the script has finished checking for all customers, you will find a folder on your desktop named ‘ATPSettings’. This folder will have an excel file that list all of your customers and has designations on if they have a Safe Links or Safe Attachments policy in place.
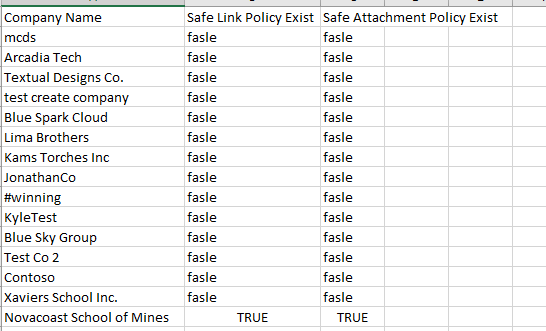
Conclusion
I believe you should run a script like this about once a quarter to ensure all customers under management have the correct policies in place for protection.
