Safe Attachment policies are a powerful feature in Defender for Office 365. They allow you to leverage a virtual sandbox to check attachments in inbound email message before they are delivered to the recipient. In addition, safe attachments also allow you to protect files in Teams, SharePoint, and OneDrive so that users aren’t inadvertently sharing malicious files. In today’s article, I am going to share some best practices when you create these policies as they are not set by default.
Licensing
The ability to create Safe Attachments comes with the Defender for Office 365 Plan 1 offering. This can be purchased standalone as an add-on or it can be baked into certain plans. In SMB, Microsoft 365 Business Premium includes Defender for Office 365.

Best Practices
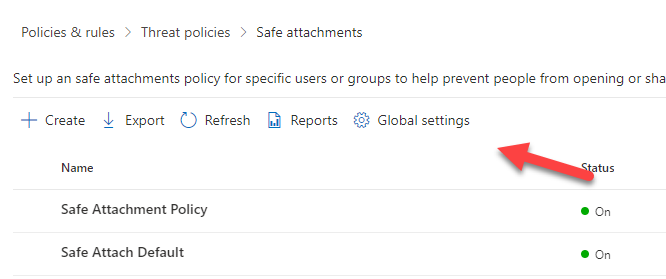
1. Ensure Global settings are configured to protect SharePoint, OneDrive, and Teams files.
This policy isn’t turned on by default and can easily be overlooked. Go to Security.microsoft.com>Email and Collaboration>Policies and Settings>Threat Policies>Safe Attachments>Global Settings>Toggle On:

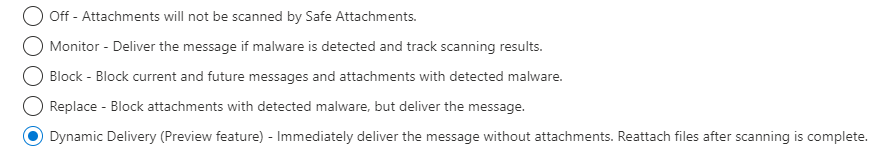
2. Use Dynamic Delivery
The Dynamic delivery option in the settings allows you to send the body of the message to the user while the attachment is still being scanned. This ensures no latency on delivery of the email body which can help avoid helpdesk calls from end users. The larger the attachment, the longer its going to take to deliver the email. If you don’t use dynamic delivery, you could experience email latency of 5+ minutes for larger attachments. Dynamic delivery allows ensures you use the admin quarantine policy so that users cannot release these messages out of quarantine themselves.
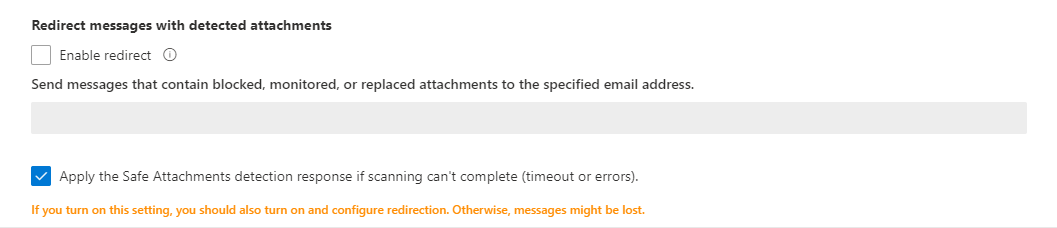
3. Apply the Safe Attachments detection response
You have an option to decide what to do if the scan either times out or errors. To be safe, you should treat this as malicious vs allowing the attachment to send on to the user. Add a redirect email to a safe account where further test can be performed on the attachment for malicious content.
4. Perform a pilot with a group of users
It’s always a best practice to not roll out a policy like this globally to an organization without doing some testing. There is a possibility some content being shared could be flagged as a false positive from Microsoft. Rather than disrupt a ton of workflows and have many helpdesk calls, run a two-week proof of concept with some of the power users within the organization.
End-User Experience
Leveraging Dynamic Delivery, a user gets the body of the email and a message letting them know their attachment is being scanned.
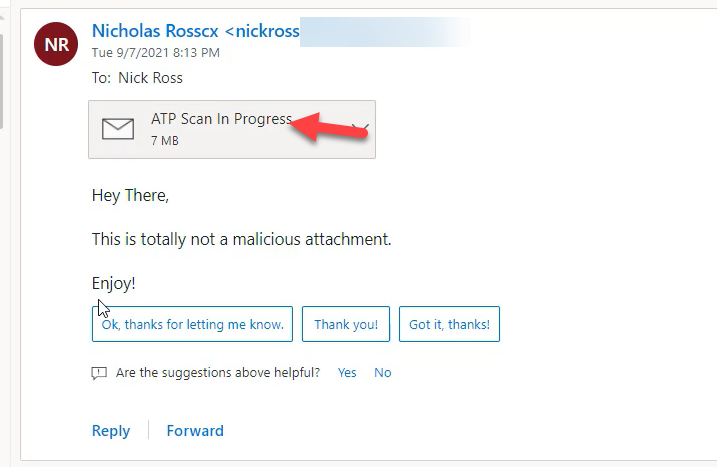
If a user was to click into the attachment, they will get more info about what is going on.
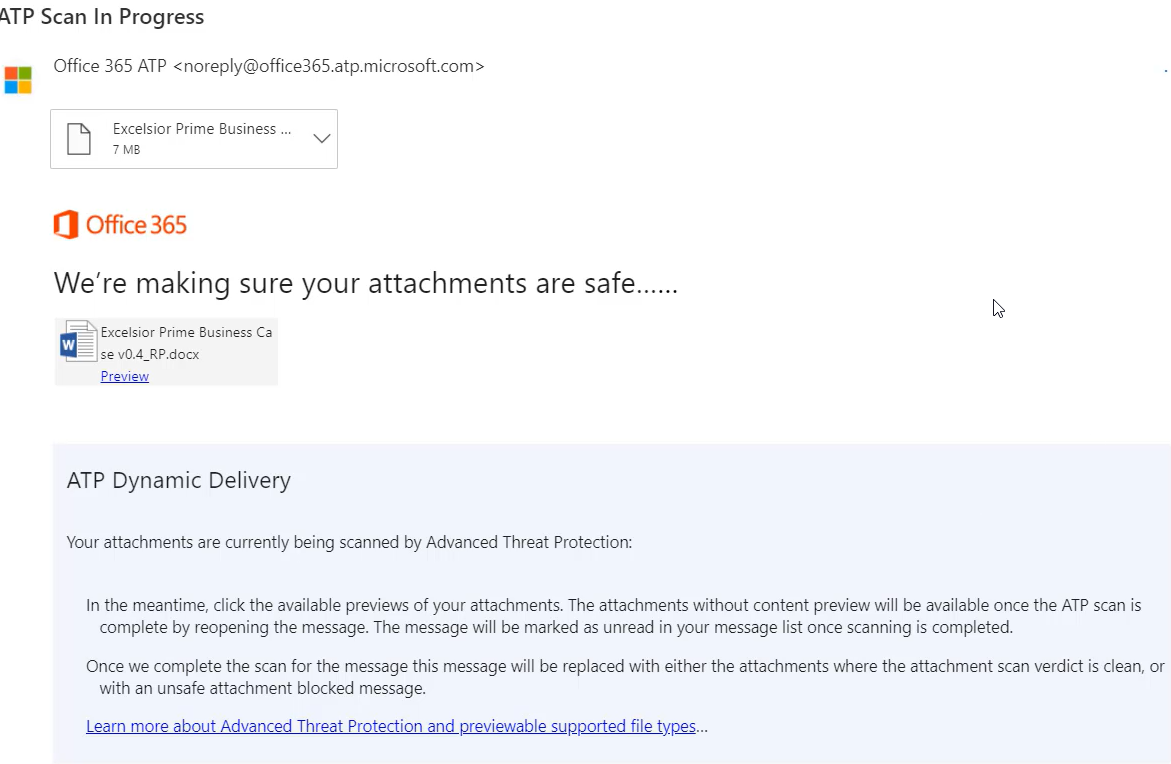
Once the scan is complete, the message will be marked as unread and the attachment will be available.
Helpful Resources
Set up Safe Attachment Policies: Set up Safe Attachments policies in Microsoft Defender for Office 365 – Office 365 | Microsoft Docs
Turn on Safe Attachments for SP, OD, and Teams: Turn on Safe Attachments for SharePoint, OneDrive, and Microsoft Teams – Office 365 | Microsoft Docs